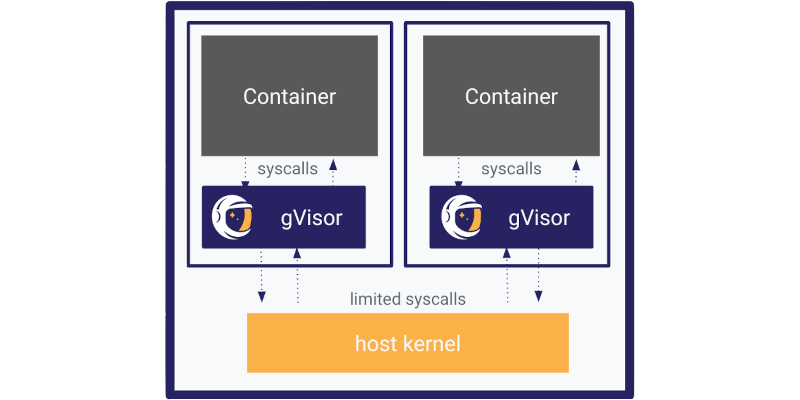
gVisor is the missing security layer for running containers efficiently and securely.
gVisor is an open-source Linux-compatible sandbox that runs anywhere existing container tooling does. It enables cloud-native container security and portability. gVisor leverages years of experience isolating production workloads at Google.
Run Untrusted Code
Isolate Linux hosts from containers so you can safely run user-uploaded, LLM-generated, or third-party code. Add defense-in-depth measures to your stack, bringing additional security to your infrastructure.

Protect Workloads & Infrastructure
Fortify hosts and containers against escapes and privilege escalation CVEs, enabling strong isolation for security-critical workloads as well as multi-tenant safety.
Reduce Risk
Deliver runtime visibility that integrates with popular threat detection tools to quickly identify threats, generate alerts, and enforce policies.
